Video surveillance cybersecurity is drawing renewed focus among IT professionals because of its essential nature in protecting the data that brings success to organizations in both the public and private sectors. Pictures don’t lie. This is why video surveillance cameras are such a powerful tool. Law enforcement, enterprise security and manufacturing are just three of countless verticals where video surveillance is being leveraged to eradicate error, monitor employees and stop crime with unprecedented success.
Businesses use video to train, to observe, and to secure. Disruption of any kind, including hacking and tampering with video surveillance equipment, can cost business owners time and money. From the other side of the world over 3G or 4G networks, cyber criminals can hack a network device using weak passwords or back doors in old operating systems to spy, steal files and hijack video surveillance cameras. Sadly, IT teams don’t always take steps that can severely limit cybersecurity hacks by following a few simple processes. Timely updates for operating systems, testing for vulnerabilities, implementing employee controls and policies, and leveraging experts can diminish if not eradicate many of these threat opportunities.
The 5 Ps of Video-Surveillance Cybersecurity Best Practices
According to ZDNET, in most cases it takes companies about six months to detect a data breach. That’s why it’s better to take proactive steps to protect against them at the outset. To stay ahead of cyber threats, your organization must take a proactive cybersecurity approach. By maintaining an aggressive focus on video surveillance best practices, your organization can be miles ahead of the pack. Successfully insulating your network is a direct result of defining and consistently following a cybersecurity best practice process. Following are the five best-practices words beginning with “P” to help you remember them.
- Password
- Permissions
- Platform
- Probe
- People
If your company is looking to improve your security posture, the following disciplines will strongly position your company for cybersecurity success.
1. Password: Avoid Manufacturer’s Default Settings
It might surprise you to know that hackers invest as much money developing their software and tools as the big corporations do to develop theirs. Consequently, there are quite a few complex hacker applications that can easily decipher simple passwords. Add to this the practice of video manufacturers publishing these default usernames and passwords on their websites, and you have a recipe for disaster. One key to eliminating this risk is to implement strong password requirements in your organization—the more complex and random, the better.
Another parallel step is to have network engineers configure IP video and network-based cameras on different ports than the ones programmed in manufacturer factory settings. Hackers use default ports to locate, infiltrate and test for vulnerabilities on recorders, cameras and other IP-based devices. Selecting different ports in a video security camera can throw up a roadblock making the hack substantially more time consuming and even propel the hacker to move on to other victims.
2. Permissions: Network Access Controls
Organizations can amplify the security of sensitive data by strictly limiting the numbers of users privileged with access to video surveillance networks and equipment. The fewer the number of employees exposed to the system’s components or data, the less open it will be to vulnerabilities, including cybersecurity breaches.
Convenience is the reason most cybersecurity breaches occur. There’s no such thing as a secure single factor login. – Shahid Shah, CEO of Netspective Communications.
Implement comprehensive vetting and selection processes to identify the people who will have access to specific data sets and equipment. By tracking the movement of particular end-users cross-network, those tasked with overseeing security can make informed decisions and design policies to keep access to a minimum. Suspicious activity should result in suspended access privileges until it can be investigated. Use biometric access technologies to control physical access, such as retinal scanners, for areas where sensitive information is accessed.
3. Platform: Inventory and Monitor All Connected Devices
One way to bolster your video surveillance cybersecurity is to inventory who and what are on your company network. The IoT is helping with this discipline because devices are now talking to each other. That’s where software platforms are paying big dividends. These with periodic security audits are a powerful way to stay abreast of employee activity.
Going department by department and reviewing current and legacy data, resource structure and how your enterprise operates end-to-end can also expose areas where additional verifications and training may be needed. The weakest link in the cybersecurity chain is well-meaning people. This type of attack is called social engineering. Video surveillance footage can help security pros understand which people have access to different assets and address potential issues of the physical operation across a campus.
At times, rogue device deployments may be discovered. A typical place for these types of devices might be in a test lab. The physical inventory process can allow your team to vet and approve or disapprove employee devices and set policies to keep data safe.
Once the inventory is complete and all devices visible on a dashboard, policies are easier to implement and tracking assets’ location and operational security becomes a process of daily maintenance.
4. Probe: Test for Cybersecurity Vulnerabilities
Because the threat landscape is constantly changing, network engineers need to conduct regular video surveillance cybersecurity vulnerability tests for all IP video cameras. Evaluate your posture on protocols like firmware updates or end-of-life equipment no longer receiving manufacturer updates. Older equipment often lacks up-to-date security fixes, providing easier access to networks. Testing helps identify gaps and prioritize replacements and workarounds to bolster security cross enterprise.
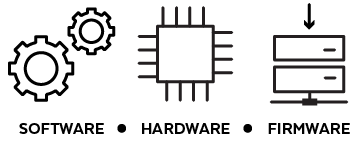
- Software. Look for unauthorized modifications in encryption communications.
- Hardware. Make sure cameras are tamper proof.
- Firmware. Run analysis for flaws and backdoors.
Automated testing eliminates errors and speeds up the process of identifying and resolving risks.
5. People: Leverage the Strengths of Your Security Team
Video surveillance cybersecurity is a complex process with a lot of moving parts. That’s why it’s critical to enlist the help of people who are in the middle of the action by consulting with internal team members and external security solutions providers.
Stakeholders within your company will know the demands of their job and be alert to red flags that others don’t encounter each day.
Service providers know the threat landscape and are constantly improving solutions through the use of algorithms and ethical hacking. They employ experts to delve into areas of your enterprise network to find gaps you might be blind to.
Find out more about PLANET’s high quality, secure IT networking devices including our extensive assortment of PoE Managed Ethernet Switches.