In the rapidly evolving cybersecurity landscape, administrators face various challenges that demand innovative solutions to safeguard their networks and data. As digital technologies become increasingly integrated into every facet of our lives, the need for advanced PoE cybersecurity solutions has never been more critical.
As technology weaves its intricate web across industries, the GS-4210-16UP4C switch emerges as a beacon of PoE cybersecurity innovation equipped with VLAN segmentation, Quality of Service (QoS) optimization, port security, and other dynamic attributes that mirror the challenges and aspirations of cybersecurity leaders.
What is Power over Ethernet (PoE) Technology?
Power over Ethernet (PoE) is a revolutionary technology that allows the simultaneous transmission of electrical power and data over the same Ethernet cable. Traditionally, Ethernet cables were solely used for data transmission, requiring separate power sources for devices. However, PoE eliminates this need by delivering power directly through the same line that transmits data. This technology was initially developed to power Voice over IP (VoIP) phones, security cameras, and wireless access points, but its applications have expanded to include various IoT devices.
PoE Switches
Power over Ethernet (PoE) switches connect devices within a local area network (LAN), facilitating efficient data communication. These switches provide data connectivity and electrical power to PoE-enabled devices, eliminating the need for separate power connections.
Features of PoE Switches
- Power Budget: The power budget of a PoE switch indicates the maximum amount of power it can provide to connected devices. Different devices have varying power requirements, so selecting a PoE switch with an appropriate power budget is crucial.
- Port Count: Consider the number of PoE ports required to connect all the powered devices. Ensure the switch has enough ports to accommodate your current and future needs.
- SFP (Small Form-factor Pluggable) Ports: SFP ports allow fiber-optic or copper transceiver modules, enabling longer-distance connections and network expansion.
- Access and Monitoring Controls: Look for features like VLAN support, QoS settings, and port mirroring for improved network control, performance, and troubleshooting.
What Types of Features Are More Secure?
- IP Source Guard: IP Source Guard prevents IP spoofing attacks by binding IP addresses to specific switch ports. This prevents unauthorized IP addresses from sending traffic through that particular port.
- DHCP Snooping: DHCP snooping prevents rogue DHCP servers from distributing incorrect IP addresses, mitigating man-in-the-middle attacks and unauthorized network access.
- SSH/TLS Encryption: Secure Shell (SSH) and Transport Layer Security (TLS) provide encrypted communication between devices and the switch, protecting sensitive information from eavesdropping.
- ARP Inspection: Address Resolution Protocol (ARP) inspection validates ARP packets to prevent ARP spoofing attacks, which can lead to unauthorized network access and traffic redirection.
- User Privilege Level Control: This feature ensures that only authorized users can access specific configuration settings on the switch. It prevents unauthorized users from making critical changes.
Implementing these features strengthens your network’s security posture by safeguarding against common attack vectors and vulnerabilities. However, balancing security and usability is essential to avoid making the network overly complex or challenging.
Managed vs. Unmanaged Switches
Managed switches provide administrators with a higher degree of control over their network environment. These switches are typically employed in more complex network setups, such as businesses, enterprises, data centers, and larger organizations, where precise control, optimization, and security are paramount.
Unmanaged switches operate with plug-and-play simplicity, requiring minimal configuration. They provide basic connectivity for devices within a network without the advanced control, customization, and monitoring features of managed switches.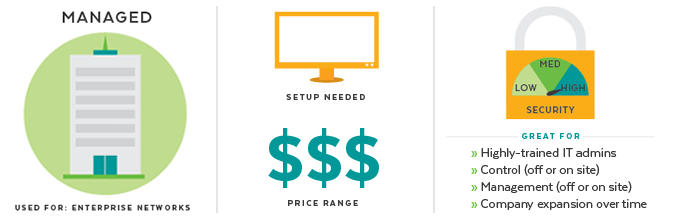
PoE Cybersecurity Switch Selection Criteria
When choosing between managed and unmanaged switches, it’s vital to understand the differences in features, capabilities, and suitability, depending on your specific network requirements.
- Power Budget: Calculate the power requirements of your PoE devices and choose a switch with a power budget that can accommodate them.
- Port Count: Ensure the switch has enough PoE ports to connect all your powered devices. Consider future growth when determining port count.
- SFP Compatibility: If you need to extend network distances or connect to fiber-optic networks, choose a switch with SFP ports.
- Access and Monitoring Controls: Choose a switch with VLAN support, QoS settings, and port mirroring capabilities to optimize performance and simplify troubleshooting.
- Redundancy and Resilience: Consider switches with redundant power supplies and support for link aggregation or STP variants for critical applications.
- Budget: Evaluate your budget constraints and balance your feature requirements with the available funds.
- Scalability: Select a switch that aligns with your network’s current size and growth expectations.
- Vendor Reputation: Opt for switches from reputable vendors known for quality and reliable customer support.
What is Better About a Managed Switch?
Segmentation of VLANs
Managed switches allow for VLAN segmentation, which is crucial for network security. VLANs create isolated virtual networks within a physical network, preventing unauthorized access and limiting the scope of potential security breaches. This enhances network security by isolating traffic and reducing the attack surface.
Turn Off/On Security Feature Sets
PoE managed switches provide the flexibility to enable or disable specific security features based on the requirements of different devices or users. This granularity ensures that security measures are tailored to the needs of the network, optimizing both security and performance.
What Types of Risks Should I Be Aware Of?
While managed switches offer advanced security features, there are some risks and considerations to keep in mind:
- Configuration Complexity: Managed switches can be more complex to configure and manage compared to unmanaged switches. Misconfigurations could lead to security vulnerabilities.
- Human Error: Errors during the configuration process can inadvertently weaken security measures, potentially exposing the network to risks.
- Lack of Updates: Failing to update the switch’s firmware and security patches regularly can leave the network vulnerable to known exploits.
How Does a PoE Managed Switch Help Keep Networks More Secure?
In today’s interconnected world, network security is a top priority for organizations of all sizes. Power over Ethernet (PoE) managed switches offer a range of advanced features that contribute significantly to keeping networks more secure.
However, it’s important to note that no single solution can guarantee absolute security, and a comprehensive network security strategy should include multiple layers of protection.
Here is why a managed switch is better suited to enhance PoE cybersecurity and how it mitigates various threats:
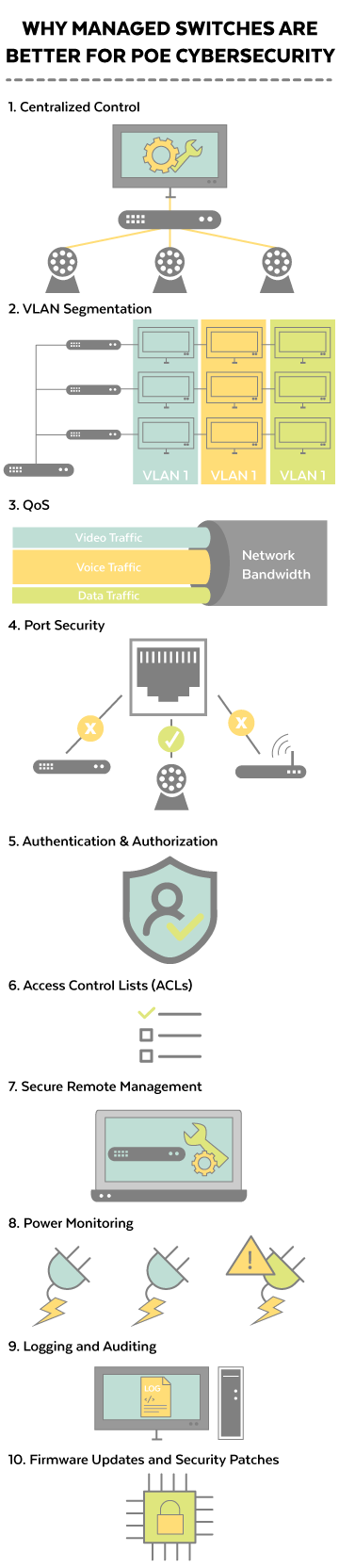
1. Centralized Control
PoE managed switches provide centralized control over network configurations and security settings. Network administrators can access a single interface to monitor and manage connected devices, making identifying and addressing security vulnerabilities remotely easier.
2. VLAN Segmentation
VLAN segmentation allows administrators to separate the network into isolated segments logically. This prevents unauthorized access and limits the potential impact of security breaches. Devices on different VLANs have limited communication, reducing the attack surface for malicious actors.
3. Quality of Service (QoS)
QoS settings on a managed switch enable administrators to prioritize specific types of network traffic. This ensures critical applications receive the necessary bandwidth, preventing network congestion and maintaining optimal performance. Besides, administrators are able to mitigate the impact of denial of service (DoS) attacks and maintain network availability.
4. Port Security
Port security features enable administrators to specify which devices can connect to individual switch ports, i.e., limit the number of devices that can access individual MAC addresses. Unauthorized devices attempting to connect are automatically blocked, reducing the risk of unauthorized access or malicious activity.
5. Authentication and Authorization
Managed switches support authentication and authorization mechanisms, such as 802.1X, RADIUS, or TACACS+, ensuring only authorized devices and users can access the network. This provides an additional layer of security and prevents unauthorized users from gaining entry, and helps maintain the integrity of the network.
6. Access Control Lists (ACLs)
ACLs allow administrators to define rules for which traffic is allowed or denied based on source and destination IP addresses, protocols, and ports. This granular control helps prevent unauthorized data transfers and stops potential threats.
7. Secure Remote Management
Managed switches often offer secure remote management capabilities through encrypted protocols. This allows administrators to manage the switch and monitor the network remotely without compromising security.
8. Power Monitoring
Managed switches provide insights into power consumption for connected devices. Unusual power consumption patterns could indicate unauthorized device connections or potential security breaches, prompting an investigation.
9. Logging and Auditing
Managed switches offer detailed logs and auditing capabilities, recording network activities and changes. This information is crucial for identifying and investigating security incidents or policy violations.
10. Firmware Updates and Security Patches
Regular firmware updates and security patches provided by the switch manufacturer help keep the device and its features up to date. This ensures that known vulnerabilities are addressed promptly, and the switch remains resilient against emerging threats.
Enhancing PoE Cybersecurity: Discover the Future of Network Security
In an era where cyber threats continue to evolve and grow in sophistication, leveraging innovative technologies like enhanced PoE can provide a valuable layer of defense for your digital infrastructure. Explore how Power over Ethernet enhances your defenses, and discover key strategies to safeguard your digital assets. Contact us today to dive into the world of PoE cybersecurity.