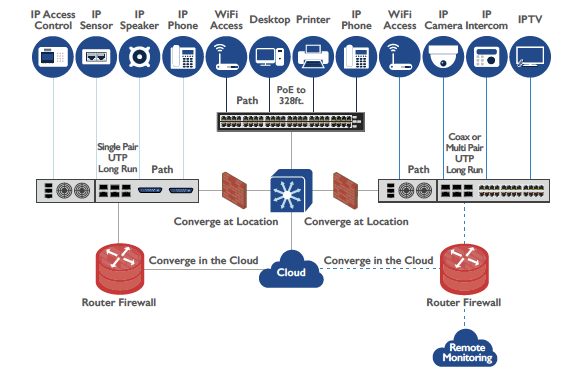
As we draw closer to the year 2020, one that experts look to as the IoT 20-billion-device point, it may be time to consider something. Does our approach toward the actual IoT network itself need a rethink?
Networks, in their continuing quest for greater and greater bandwidth, were originally designed to support the PC. An ecosystem that included software systems, computers, phones, security cameras, and employee badge access points has gradually evolved into something more sophisticated.
This new multi-layered network has a different set of demands. Added to the PC centric arm of switch, cable and device configuration, you can also find mobile and wireless support, thin-clients and SaaS platforms, and off-site cloud services. What was once housed under one roof or on one campus, now extends across states and even regions.
This new topology is scalable, discipline-specific and remotely accessible. While highly beneficial to the end user, it also brings with it a new set of security risks and topographical complexities.
Where to begin the change process
To advance functionality, the IT professional will want to hold potential improvements up and filter them according to these questions:
- Is this change cost-effective?
- Has the disruption caused by this change been reduced to a minimum?
- Is this change sustainable?
- Does this change align with our business priorities?
- Will this change deliver meaningful improvements?
In the past, advancement consisted of bandwidth expansion, server adds, and workload balancing to support software applications that, in turn, supported business operations. That is what drove IT development.
Today, things like mobile devices including Bring-Your-Own-Device (BYOD) programs with all of the expected security considerations have added complexity. The installer and the IT manager are tasked with consolidating these pieces into one well-working unit.
Managing a newer set of endpoints
A managed switch, for instance, should be chosen wherever access levels to sensitive data are being supported. A managed switch allows administrators the ability to determine criteria for access to different LANs at the port level.
A managed switch is also a desirable choice when IT administrators need to access security systems or shut down ports remotely. Intelligent devices are needed for an increasingly connected business enterprise model.
The new generation network will continue to support unique, far-flung internal LANs and WANs while also enabling access to external platforms. Rare is the medium or large-sized organization that does not deploy at least one API middleware system or external platform like SAP Supply Chain Logistics or Salesforce.
Another external resource that has become increasingly relevant as older hardware is decommissioned is the cloud. Companies are migrating their data and systems to cloud server operations like AWS, Microsoft Azure, or Google Cloud Platform. That means a link to the outside. With that link also comes exposure.
All of these added local area network configurations invite a new range of challenges. In a recent study, Frost & Sullivan discusses this very thing. How will the 2020 IT local area network stack up against its earlier iteration? In other words, where can we expect to see change?
Think like an architect
When re-evaluating network paths and switch points, it’s helpful to review the current schematic for the existing switches and infrastructure from and end-user perspective, to understand how they can best fit into the physical location. Installers don’t always have the luxury of adding a network closet to accommodate a new loc, but it’s surprising what can be done when there is a clear picture of the environment.
The next step is to re-evaluate where each of these endpoints is and to gain a full understanding of the roles people play in the primary business structure. Each point provides a granular idea of what systems end-users will need to access.
NOTE: Be sure to double-check existing switches to see if they are compliant with device technologies they will be supporting. It’s possible to repurpose older switches in other locations and to replace those that support Type 3 and 4 PoE devices and so on.
Think like a cybersecurity pro
Identify serious security risks and functionally separate IP network paths by application and platform. In fact, separate networks housed on separate servers helps ensure that disruptions and intrusions don’t happen.
Single cable connections between these critical intellectual repositories helps eliminate unwanted exposure to other network areas. The practice of network segregation helps to isolate access points and minimize exposure when situations do occur.
Consider network segregation to isolate cloud-managed endpoints and minimize security or network-breach exposure. Modern LAN designs must account for multiple application and management platforms, including on-premises, server-based applications, cloud-based platforms and hybrid solutions.
The Modern LAN: Rethinking Network Design for the Modern Age, Frost & Sullivan
Think like the cost accounting department
Let’s face it, any time you find a way to reuse existing devices you’re preserving budgetary resources for other purchases. One area that has developed into an entire sub-industry is Power over Ethernet (PoE). The reuse of Cat5e and Cat6 twisted pair cable infrastructure has literally saved organizations millions in rewiring.
Another technology that is following suit is G.Fast. The whole purpose behind this new ultrafast broadband was to find ways to eliminate cable pulls while achieving ultrafast broadband service.
By eliminating cable pulls, contractors eliminate disruption for businesses, students, and government organizations that would otherwise need to work around this noisy, often dusty process.
Conclusion
What could be more energizing for the IT pro than a budding technological era when the SMART device comes alive? The role and complexity of this new age will redefine how IT functions within the framework of an organization.
Remote access and cross-platform visibility of entire systems will demand that IT takes a broader role within the management of physical facilities.
As we have also seen, the local area network itself is transforming and the way it is configured will improve efficiency, security, and all while saving money.
If you enjoyed this article, please feel free to subscribe. You can also follow us on Twitter.