Proper management of an enterprise network, including those with an IP surveillance camera, protects network function and addresses the potential for security threats. Called a “security zone” or “zone of trust,” each part of the enterprise network must be set up to address the security levels required to protect the data it supports. This process is critical for business health and eliminates compliance risk.
The security zone categories protected in network configuration would include:
- Intellectual property and business secrets
- Sensitive information of employees and customers
- Financial information including banking information
- IP Surveillance data of physical information like access points within a property
A network security zone is an administrative name for a collection of systems that require the same access control policy. IP addresses map systems into security zones. This requires that the IP addresses used in your multi-level secure network be predictably associated with a single system or group of systems with the same access control policy. A network security zone can contain a single IP address or any combination of IP addresses and subnetworks. All IP addresses in a security zone must have the same security label, though all IP addresses with the same security label do not have to be in the same security zone.
Understanding Multi-level Security Concepts | IBM
Multi-level security networking is a way of defining and implementing a secure network environment. The use of security labels and systems makes it easier for workers to comply with the security policies within an organization.
Levels of access, logins for different systems, and timed sessions ensure that human error does not occur. Port of access or location where log in may occur is another tactic that eliminates unauthorized access events. Each of these disciplines helps reduce the risk potential.
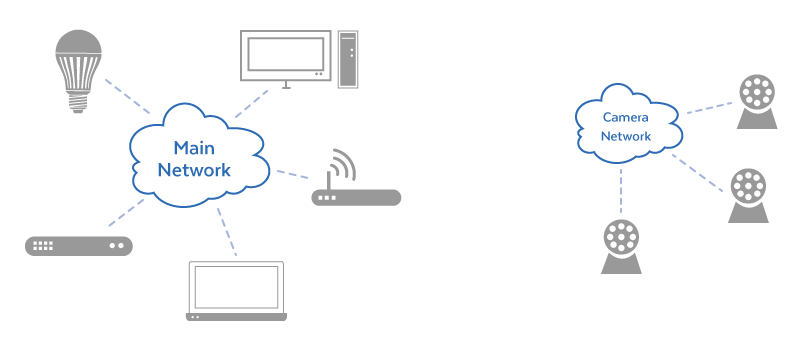
IT administrators can also support security initiatives to separate siloes like building controls and security controls from the primary enterprise network. There are, however, pros and cons to having a separate IP security camera network. For example, a smaller business may not have the resources to justify a distinct network and may rely on a landlord’s camera security system.
Whether or not an organization should separate IP cameras into their networks is both a financial and compliance-driven question. It is essential to approach this decision with an understanding of how IP surveillance cameras function.
The Inner Network Workings of IP Cameras
IP security camera networks support the same IP network protocols as most corporate enterprise networks, which is why they are often on the same network. All information recorded by an IP Camera is compressed, and files transmitted (wired or wireless) over a network to be stored in digital form on servers. The advantage of IP cameras is that they produce high-resolution images and use SSL/TLS data encryption, reducing vulnerability to hacking.
Hacked IP cameras can expose retail outlets, financial institutions and building security services to risk. That’s because they can be accessed remotely, making them a ripe target for hackers.
One: Security Access to Separate IP Cameras Networks Is Easier to Manage
When on a different network, cameras do not impact other systems on the main network. This further limits the user access to only those managing IP security within an organization, which are a subset of the overall number of employees. There are fewer passwords to protect and access points to monitor.
Two: Unusual Activity on Separate Networks Is Easier to Spot
Tracking files and leveraging IP security system controls are simpler to manage within the smaller access group of users on a separate network. Further, bandwidth not budgeted between countless other end users opens up for image data. The additional space facilitates the management of high definition images. Unusual activity or file transfers can alert security teams to investigate. When urgencies occur, a dedicated network is under the care of dedicated staff.
Three: Separate IP Camera Networks Bolster Compliance
Many companies are now using thermal imaging features in the IP camera system to watch for people with high temperatures upon entry on-premises in the morning to protect employees from the spread of COVID. Now that people are returning to work en masse, this capability will allow security teams to screen discreetly and follow up quickly.
Having camera files separate from the primary enterprise network ensures that companies comply and demonstrate due diligence in protecting sensitive information, like employee health status. This process aligns with HIPAA privacy mandates while also enabling businesses to identify if an outbreak has occurred.
Four: Network Training for Security Associates Costs Less in The Long Run
To enable security teams to operate cameras properly, they need to address issues as they arise. One common problem is capturing images in black and white when they should be recording in color. Not being able to clearly identify the color of a vehicle or clothing of a potential security risk can limit an organization’s ability to identify and prosecute perpetrators.
This issue of black and white when the image should be color can happen when the infrared switch of a camera is left on inadvertently.
A security guard with basic training will be able to troubleshoot problems like this on the go, helping to maintain optimum functioning of equipment.
Though this kind of training can be a financial investment, the results may far outweigh the upfront expense. Camera security vendors may also be able to provide support, which may involve added expense but be more cost-effective than hiring extra IT admins.
Local IP Networks Are Cost-Effective to Run
A separate local IP surveillance network operates on Layer 2. As a refresher, the OSI (Open Systems Interconnection) model characterizes how devices communicate.
- Layer 1 (Physical Layer): data bits over physical mediums
- Layer 2 (Link Layer): data frames between connected nodes on the physical layer
- Layer 3 (Network Layer): addresses routing and traffic control on a multi-node network
Enterprise networks generally operate on layer 3. By transmitting local IP security camera footage over layer 2 systems, the potential cost for equipping and operating the network is significantly less.
Final Thoughts on Separating IP Surveillance Networks
IP camera surveillance helps organizations monitor internal and external activity. Removing the potential for interference with other network subnets can ensure optimal functioning for all networks.
If you’d like help choosing the right switches or cables for your IP camera system, please reach out to our PLANET sales staff.



Join the Discussion One Comment